| Bookmark Name | Actions |
|---|
XACML based Authorization
This section explains the authentication based on Extensible Access Control Markup Language (XACML), which is an open standard XML-based language designed to configure security policies and access rights to information for web services.
It supports
- Attributes based access control definitions
- Composing of policies by re-using those low-level definitions
XACML policy model is shown below.
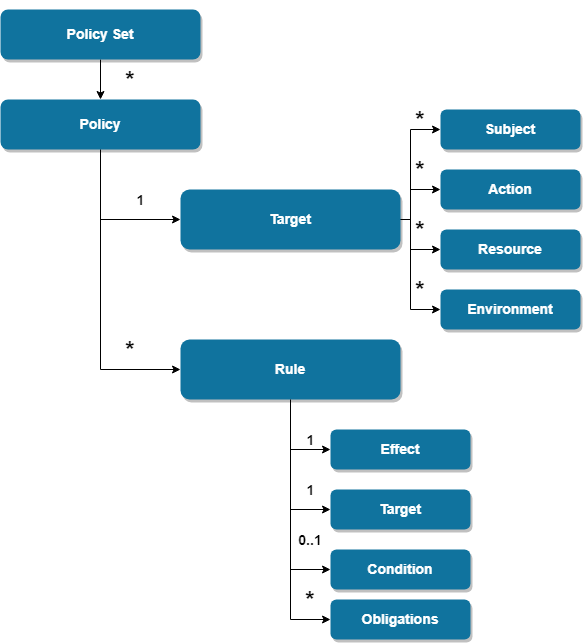
Where,
- Target is set of simplified conditions for the subject, resource and action that must be met for a policy set, policy or rule to apply to a given request
- Obligation is a directive from the Policy Decision Point (PDP) to the Policy Enforcement Point (PEP) on what must be carried out before or after access is approved.
Policy Authoring
Temenos Microservices adopted XACML implementation to allow you to define authorization policies for intended microservices. Policy Editor (Design time) is used to author XAML policies for microservices and can be deployed on the policy store.
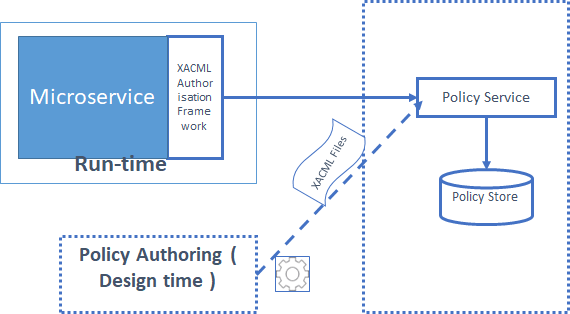
Policy Authoring is carried out using Policy Editor and final reviewed policies are uploaded into a centralized policy store.
XACML – Policy Attributes
From Microservices perspectives, the following are the attributes used to the author authorization policy.
|
S.No |
XACML Attribute Type |
Information Data available for policy enforcement |
|---|---|---|
|
1 |
RESOURCE |
The resource element is a data, service or system component Data parameters available in HTTP Request Headers & Payload and “Data Entity”. Example “Balance”, “Transaction” |
|
2 |
SUBJECT |
A subject element is an entity requesting access. User attributes available in HTTP Header. |
|
3 |
ACTION |
Action id of the API |
|
4 |
ENVIRONMENT |
Environmental parameters existing in the Business Function context. AWS – Lambda, AZURE – Function, Docker – Web container Context (Tomcat) |
Authorisation
Policy Decision Policy (PDP) engine provides infrastructure to evaluate applicable policy and returns an authorization decision to the application to enforce the decision at right enforcement point.
Out of existing options in the market, AuthzForce (OW2 https://www.ow2.org/) is identified as PDP engine for out of the box support. An adapter gets developed for AuthzForce and used for implementing policies in microservices.
Apart from the adaptor, the below component’s generic implementations are provided as a part of common library:
- Information Point
- Decision Point & Obligations
Policy Enforcement
Microservice Framework supports XACML-based authorization enforcement in all microservices. By designing the policies in individual microservices, you can restrict the access to a resource managed through microservice APIs.
To execute the XACML policies defined, the resource attribute values should be available as a part of information point in microservices. In many scenarios, these attribute values may not be available as part of respective.
The Holding Microservices have XACML Policy supported along with obligations apply restrictions on the accounts, which current query operations Holding Service support.
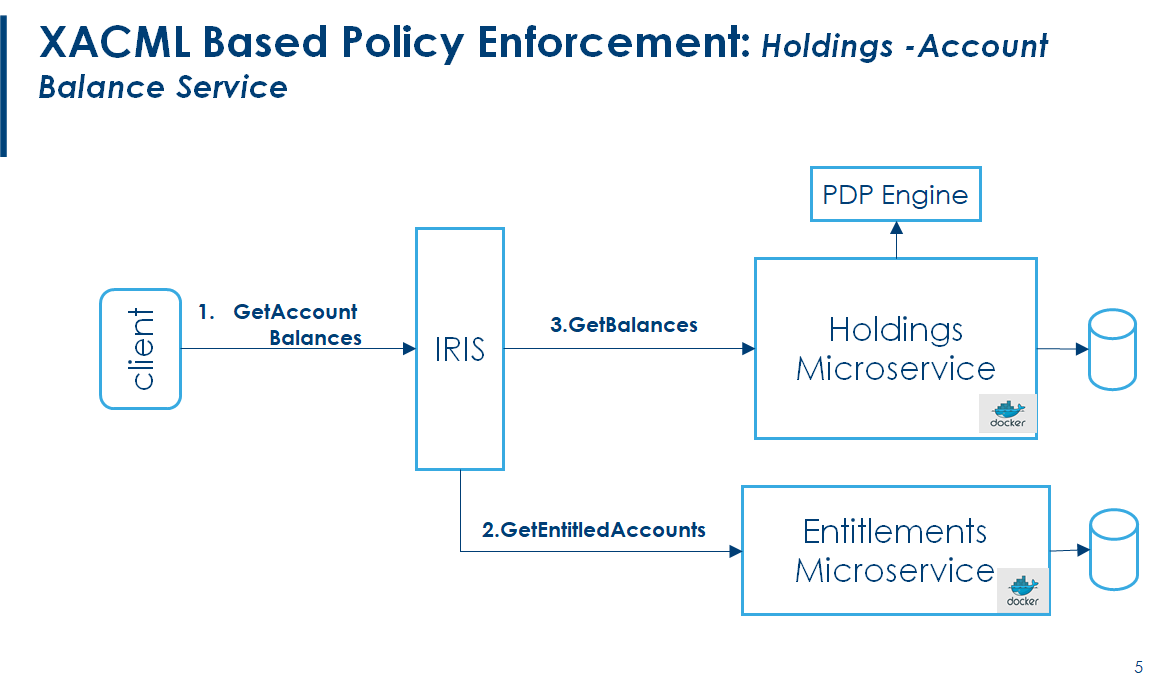
Samples
This section provides you the policy configuration for applying filters on the accounts.
If your role is either retailuser or relationshipmgr, then you can execute getBalancesForEntitledAccounts API function and only have access to one of the accounts provided in "allowed accounts" list.
<?xml version="1.0" encoding="UTF-8"?>
<PolicySet
xmlns="urn:oasis:names:tc:xacml:3.0:core:schema:wd-17"
xmlns:ns2="http://thalesgroup.com/authzforce/pdp/model/2014/12"
PolicySetId="default" Version="1.0"
PolicyCombiningAlgId="urn:oasis:names:tc:xacml:1.0:policy-combining-algorithm:first-applicable">
<Target/>
<Policy PolicyId="urn:curtiss:ba:taa:taa-1.1" RuleCombiningAlgId="urn:oasis:names:tc:xacml:1.0:rule-combining-algorithm:first-applicable" Version="1.0">
<Description>Policy for Business Authorization </Description>
<Target>
<AnyOf>
<AllOf>
<Match
MatchId="urn:oasis:names:tc:xacml:1.0:function:string-equal">
<AttributeValue
DataType="http://www.w3.org/2001/XMLSchema#string">getBalancesForEntitledAccounts</AttributeValue>
<AttributeDesignator
Category="urn:oasis:names:tc:xacml:3.0:attribute-category:resource"
AttributeId="urn:oasis:names:tc:xacml:1.0:resource:OperationId"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true" />
</Match>
</AllOf>
</AnyOf>
</Target>
<Rule RuleId="compositerules" Effect="Permit">
<Description />
<Target/>
<Condition>
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:and">
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:string-at-least-one-member-of">
<Apply FunctionId="urn:oasis:names:tc:xacml:1.0:function:string-bag">
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">retailuser</AttributeValue>
<AttributeValue DataType="http://www.w3.org/2001/XMLSchema#string">relationshipmgr</AttributeValue>
</Apply>
<AttributeDesignator
Category="urn:oasis:names:tc:xacml:3.0:attribute-category:subject"
AttributeId="urn:oasis:names:tc:xacml:1.0:subject:x-authz-user.role"
DataType="http://www.w3.org/2001/XMLSchema#string"
MustBePresent="true" />
</Apply>
</Apply>
</Condition>
<ObligationExpressions>
<ObligationExpression
ObligationId="filter-accounts" FulfillOn="Permit">
<AttributeAssignmentExpression
AttributeId="urn:oasis:names:tc:xacml:1.0:action:Operation"
Category="urn:oasis:names:tc:xacml:3.0:attribute-category:action">
<AttributeValue
DataType="http://www.w3.org/2001/XMLSchema#string">filter_in</AttributeValue>
</AttributeAssignmentExpression>
<AttributeAssignmentExpression
AttributeId="accountId"
Category="urn:oasis:names:tc:xacml:3.0:attribute-category:resource">
<AttributeDesignator
AttributeId="urn:oasis:names:tc:xacml:1.0:resource:allowedaccounts"
DataType="http://www.w3.org/2001/XMLSchema#string"
Category="urn:oasis:names:tc:xacml:3.0:attribute-category:resource"
MustBePresent="false" />
</AttributeAssignmentExpression>
</ObligationExpression>
</ObligationExpressions>
</Rule>
<Rule RuleId="deny-otherwise" Effect="Deny" >
<Target/>
</Rule>
</Policy>
</PolicySet>
Add Bookmark
save your best linksView Bookmarks
Visit your best links BACK
BACKIn this topic
Are you sure you want to log-off?